[index] [text page] [<<start] [<prev] [next>] [last>>]
Page 30: Verification by stunt DNS
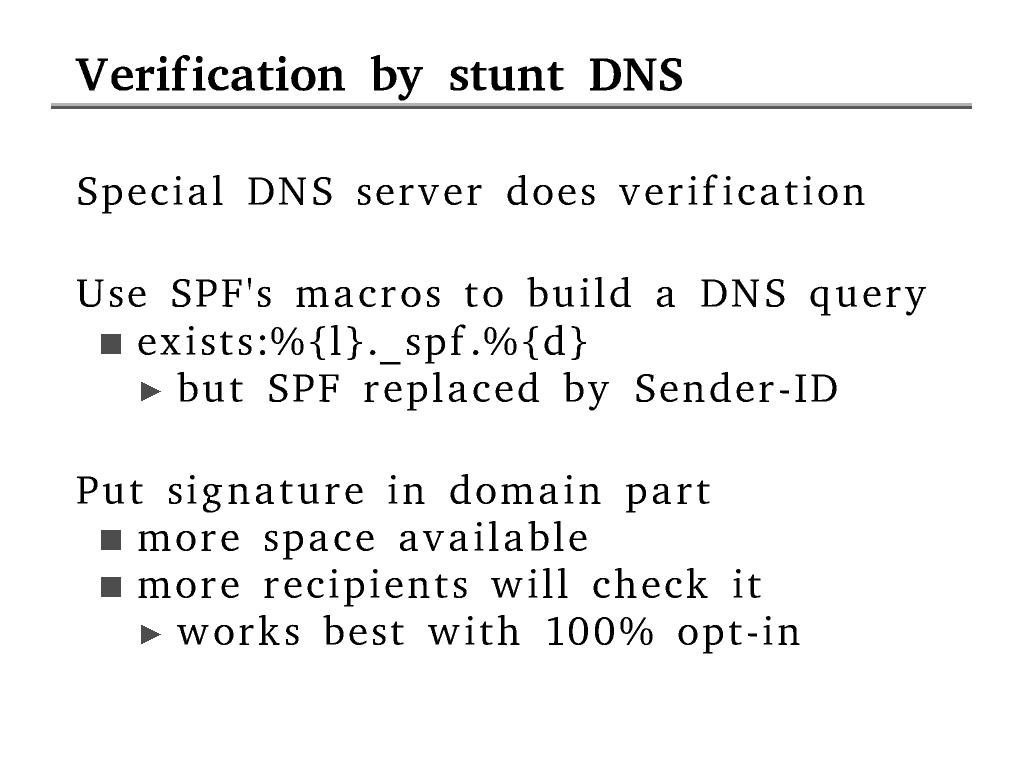
Sender-ID uses SPF records to describe policy, but it checks an
address extracted from the message header rather than the envelope
address, and addresses in headers cannot be signed. So that idea is
mostly dead in the water.
Alternatively if we put the signature and local part in the domain
part of the bounce address, then most recipients will check that its
DNS is correctly set up, i.e. they will do an MX query for the
domain which will end up at our stunt DNS server which can then
verify the signature.
This gives us really high quality information on how an address is
being used, so it makes detecting and invalidating compromised
addresses much more feasible.
It doesn't allow us to deal with joe jobs based on sending email
"from" recipient addresses such as fanf2@hermes.cam.ac.uk because
those addresses still have to work. If we have 100% use of signed
addresses then we could put hermes.cam.ac.uk in nomail.rhsbl.sorbs.net
but that won't happen. Something more subtle is needed.
Security of DNS becomes more important too.
Generated by MagicPoint
