[index] [text page] [<<start] [<prev] [next>] [last>>]
Page 26: Choice of algorithm
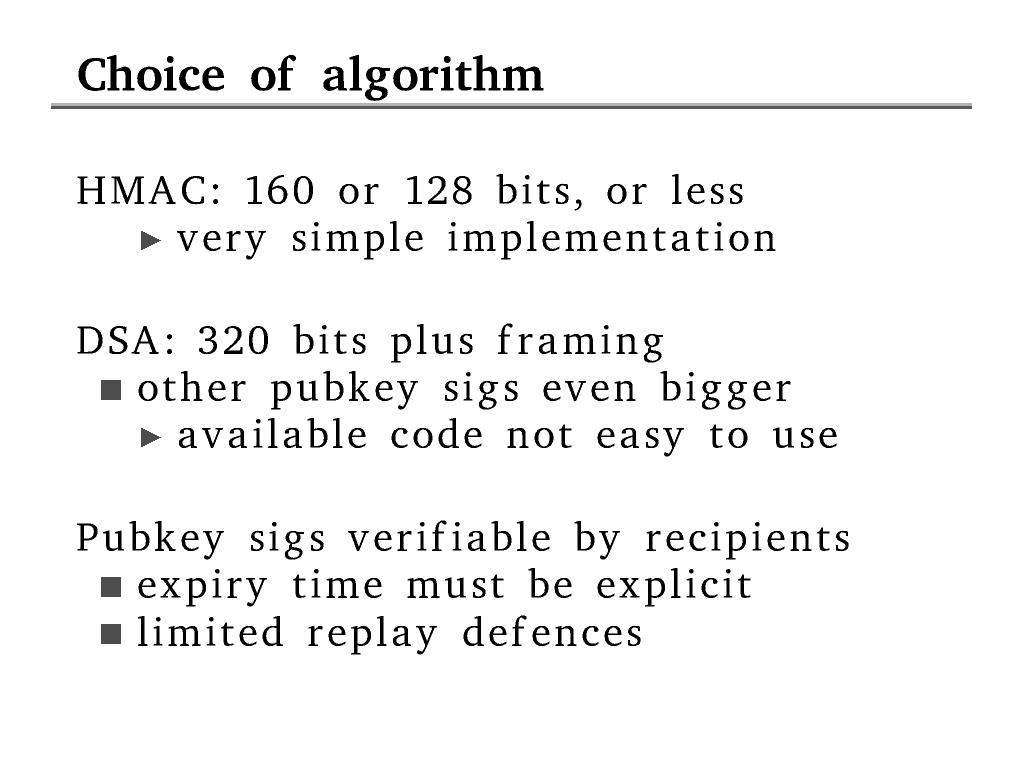
If we use HMAC we have to do all the verification because you need
to know the secret in order to verify. In order for recipients to be
able to detect forgery they must participate in a verification
protocol, discussed later.
Public key verification allows recipients to verify without help
from us, which improves the scaling properties and resistance to
overload attacks.
It also prevents us from expiring an address early if it is
compromised, which we can do if we do all the verification.
Generated by MagicPoint
