[index] [text page] [<<start] [<prev] [next>] [last>>]
Page 22: Blacklist of leaked addresses
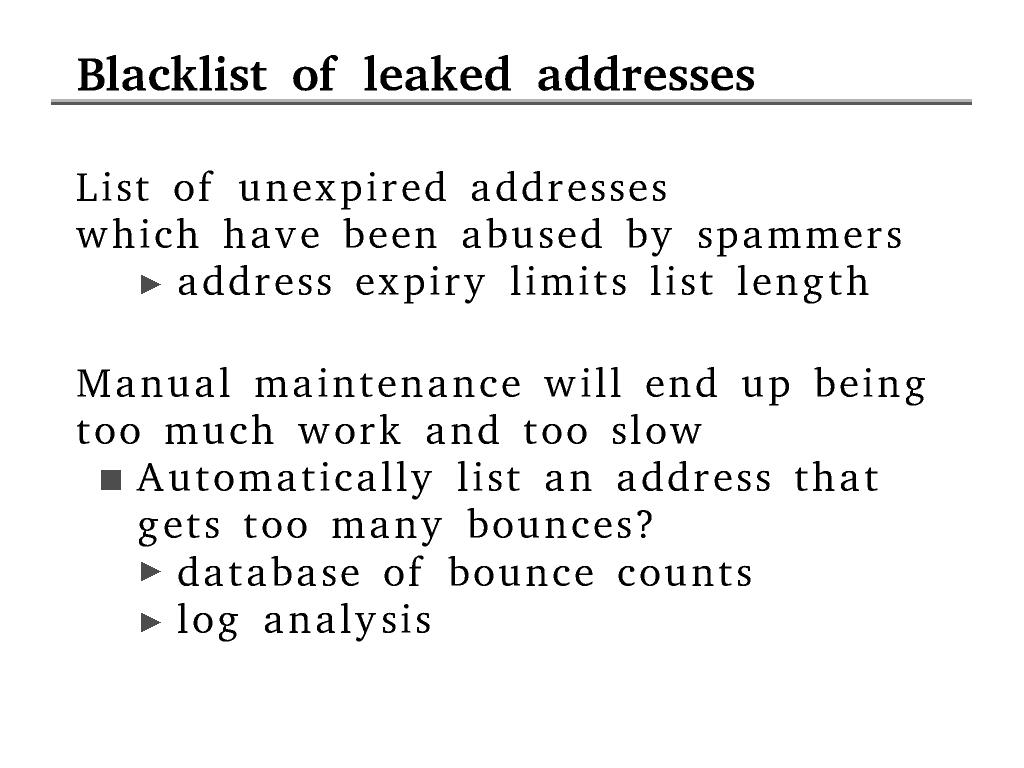
At the moment we don't know what the trigger limits should be.
They vary greatly depending on the number of recipients, which we
might not know because of alias expansion at remote sites.
The database is not so nice because it introduces state into a
system that would otherwise be stateless. However it doesn't have to
be part of the critical path -- it can be just a bag on the side
like the current log analysis and traffic graphing stuff.
Generated by MagicPoint
